1000+ Automated Security Posture Optimization
Security Checks That Fix Themselves
Scroll Down
Let ZHERO’s expert analysis engine continuously scan your Zscaler configuration for security gaps, optimization opportunities, and best practice violations — with automatic resolution proposals and one-click remediation for identified issues.
Evergrowing Library ofdivided in categories
Security Posture
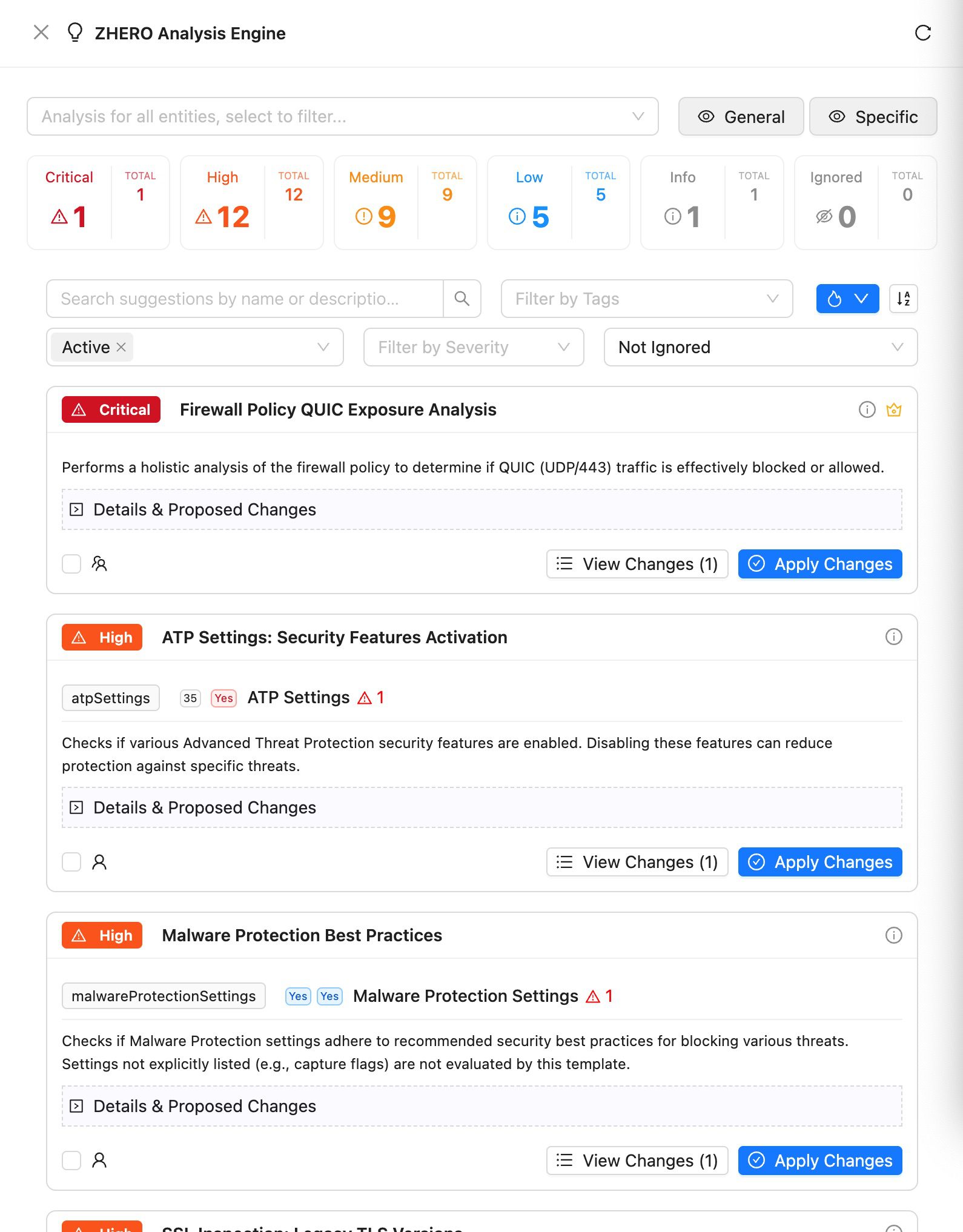
Immediate Threat Detection and Vulnerability Closure
Identify and eliminate critical security gaps before they can be exploited like:
- SSL Inspection Bypass Risks: Detect overly broad SSL exemptions that create blind spots
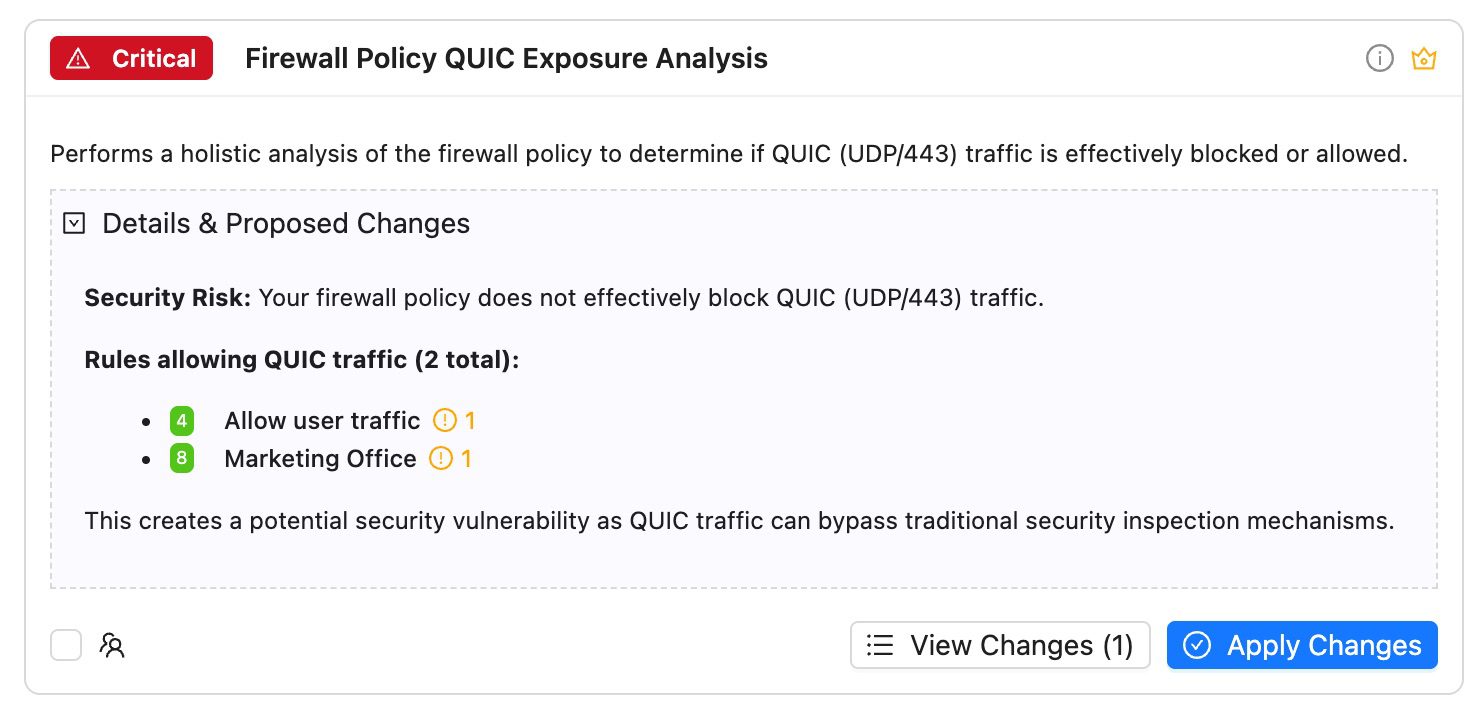
- QUIC Traffic Leaks: Identify firewall rules allowing unencrypted UDP/443 traffic
- Data Protection Holes: Discover unprotected sensitive data paths
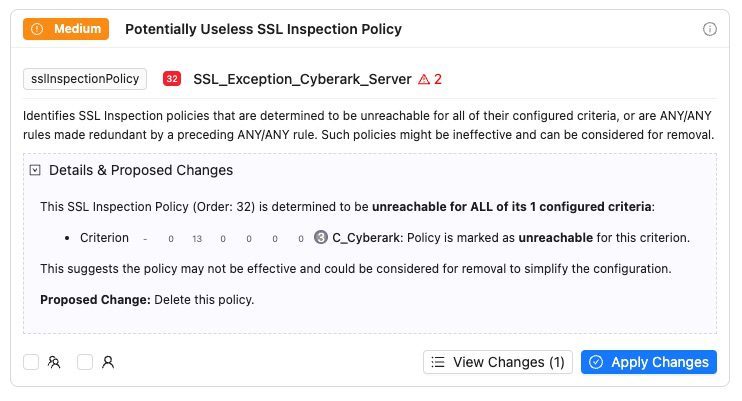
Optimization
Streamline Configuration for Maximum Performance
Eliminate redundancy and complexity to improve overall policy quality & readability, like:
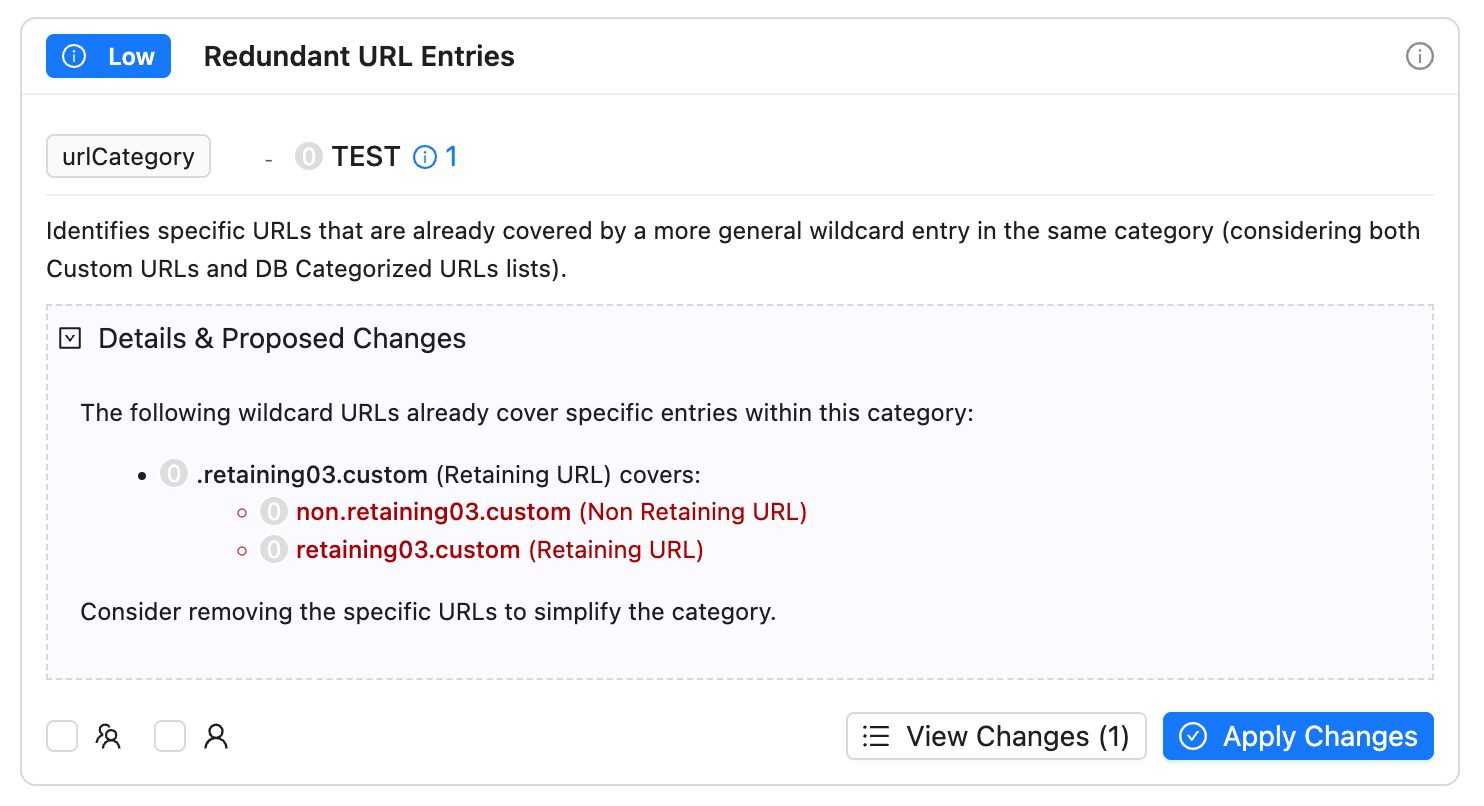
- Redundant Policies/Entities: Identify duplicate or overlapping rules that slow processing
- Unreachable Rules: Detect policies that never get evaluated
- Unused Entities: Find categories, groups, and rules with no traffic in 30+ days
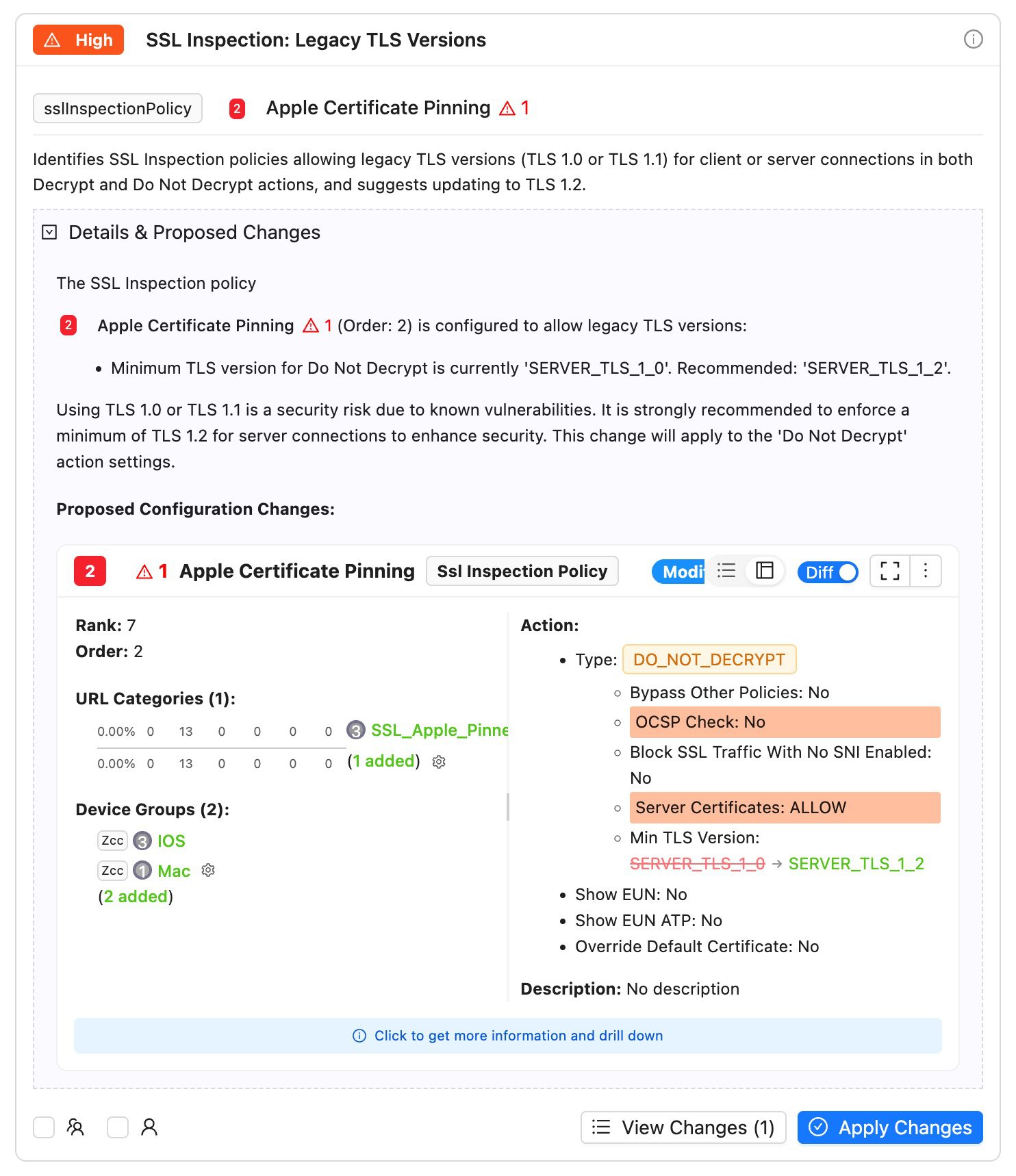
Compliance
Maintain Continuous Audit Readiness
Ensure adherence to industry standards and regulatory requirements, like:
- TLS Version Compliance: Enforce modern encryption standards (TLS 1.2+)
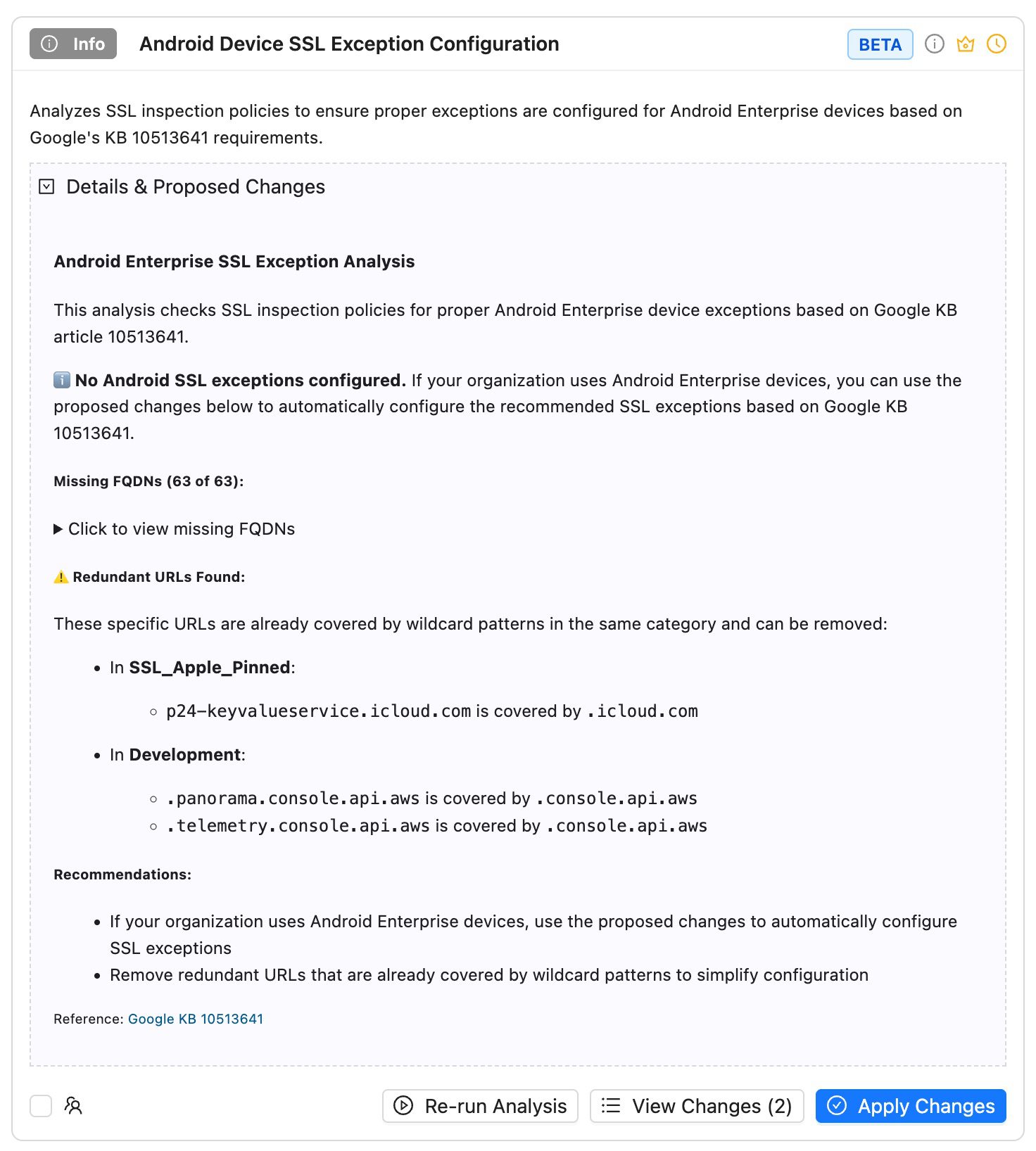
- Device Management Standards: Apple KB 101555, Google KB 10513641 compliance
- Regulatory Alignment & Industry Benchmarks
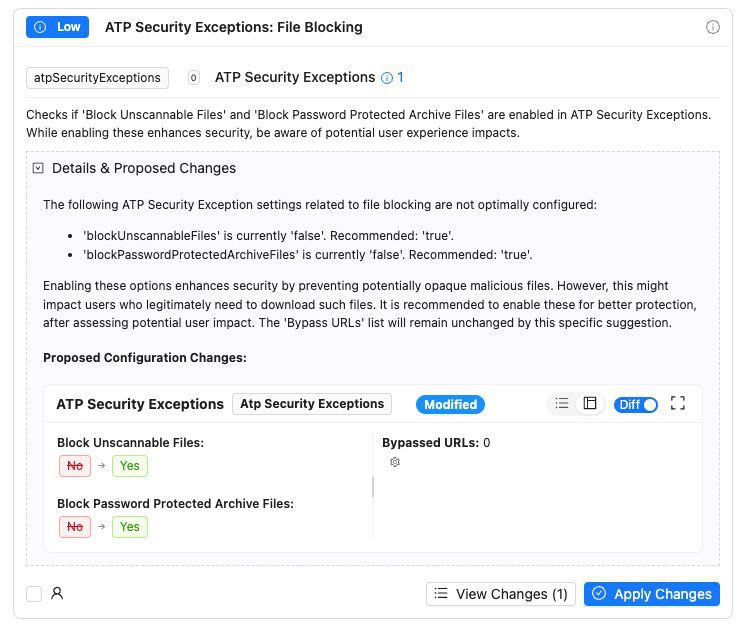
Best Practices
Expert Configuration Applied Automatically
Implement Zscaler’s recommended settings and industry best practices, like:
- Malware Protection Settings: Optimal threat prevention configuration
- ATP Risk Tolerance: Balanced security vs. user experience settings
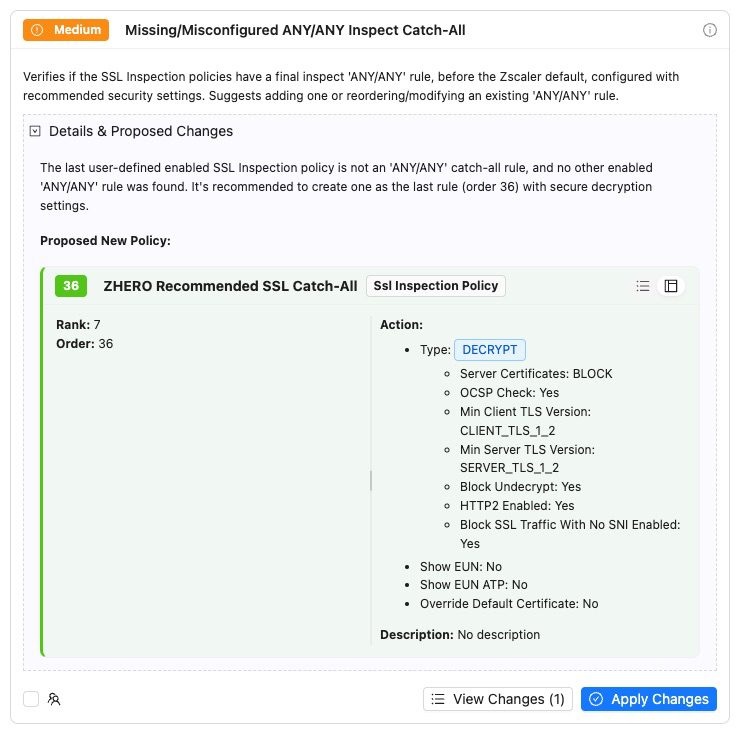
- SSL Catch-All Rules: Proper ANY/ANY rule implementation
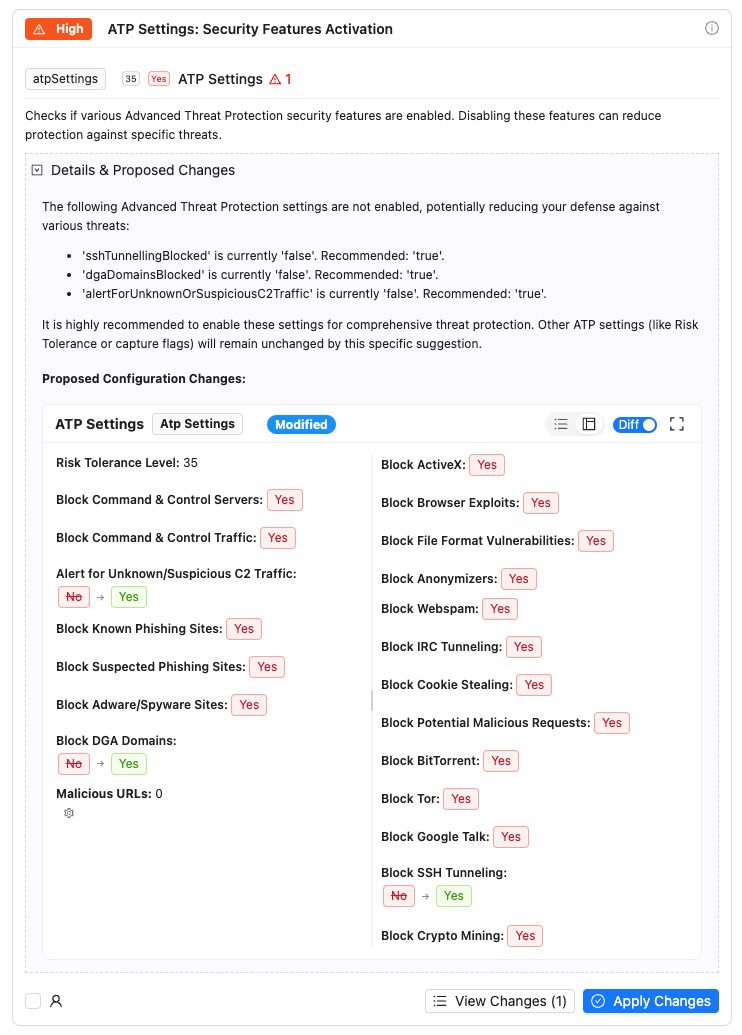
- Security Feature Activation: Enable all recommended protection features
Intelligence
Data-Driven Insights from Log Analysis
Leverage log analysis and traffic patterns for proactive optimization, like:
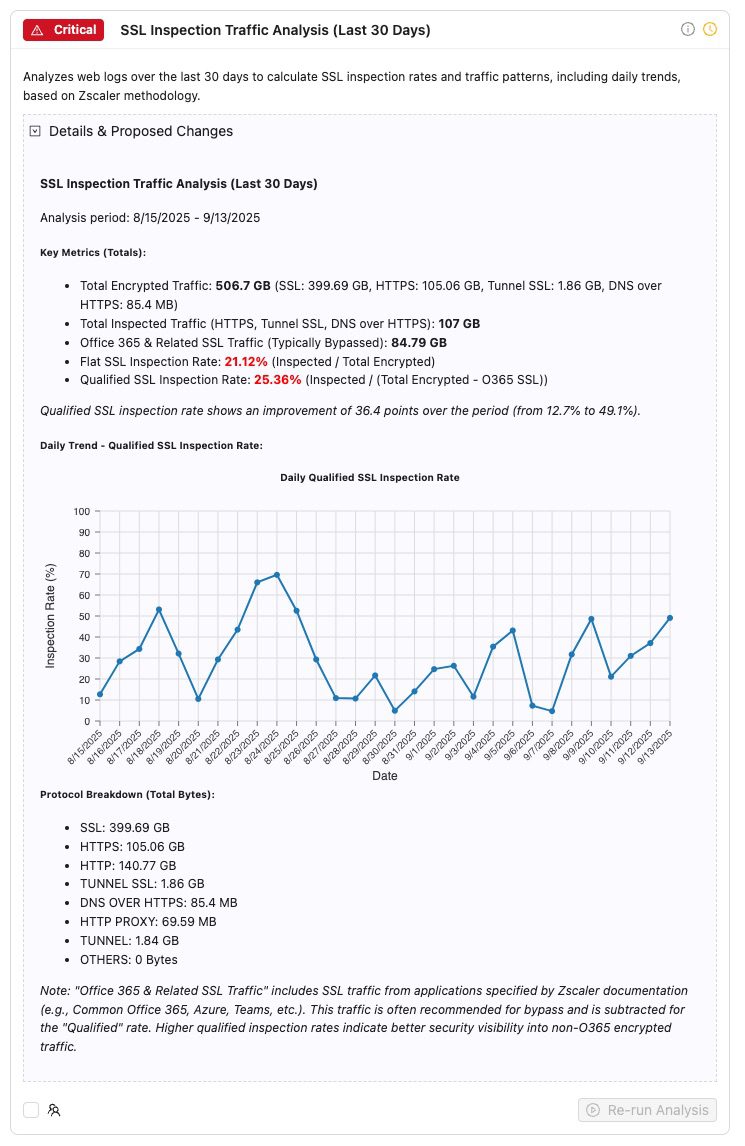
- Traffic Pattern Analysis: 30-day SSL inspection rates and trends
- Behavioral Anomalies: Unusual configuration combinations or access patterns
- Predictive Maintenance: Identify issues before they impact users
- Usage-Based Recommendations: Optimize based on actual traffic data
Core Analysis Categories
Five Dimensions of Intelligent Protection
Security Posture
Identify and eliminate critical security gaps before they can be exploited
Optimization
Eliminate redundancy and complexity to improve overall policy quality & readability
Compliance
Ensure adherence to industry standards and regulatory requirements
Best Practices
Implement Zscaler's recommended settings and industry best practices
Intelligence
Leverage log analysis and traffic patterns for proactive optimization
Intelligent Analysis in Three Steps
Whant to know more?
The Configuration Complexity Challenge
Zscaler offers hundreds of configuration options, but knowing the optimal settings requires deep expertise and constant vigilance:
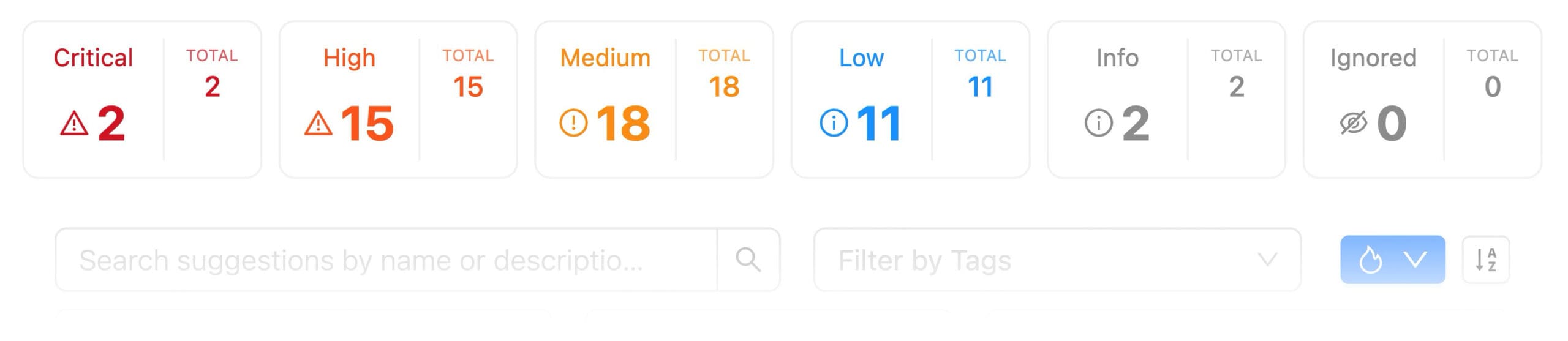
Just a few examples of our analysis templates in action:
Watch a 4 minutes demo:
Ready to Transform Your Zscaler Experience?